This documents how I configured Nextcloud to use Single Sign-on leveraging Keycloak as the identity provider. There is official documentation for a Nextcloud-Keycloak integration, but it is behind Nextcloud's paywall.... I found several other guides, some directly conflicting with each other, but piecing them together has produced a working solution.
On to getting things working:
Nextcloud configuration
Global Settings
First, ensure that you do not lock yourself out of your Nextcloud instance while configuring SSO! Set the "Global Settings" to allow multiple back-ends.
Service Provider Data
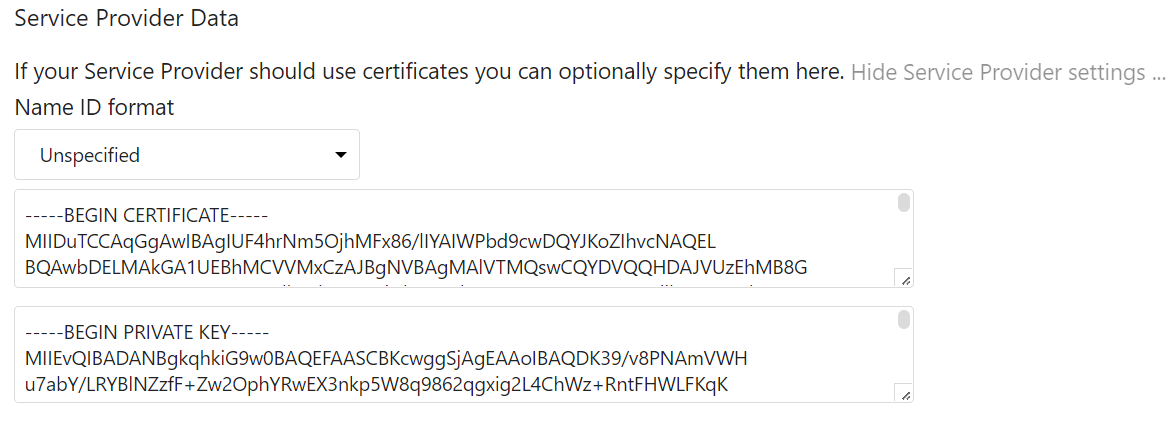
Provide a certificate for request signing. This is not publicly seen; it is only used between Nextcloud and Keycloak. I opted for a self-signed x.509 certificate. It will be imported to Keycloak as part of the metadata XML so trust will not be an issue. Fill in the certificate request using whatever information you wish.
openssl req -nodes -new -x509 -keyout private.key -out public.cert
In the Service Provider Data section enter the public certificate and the private key in the corresponding text blocks. It should look like this:
Identity Provider Data
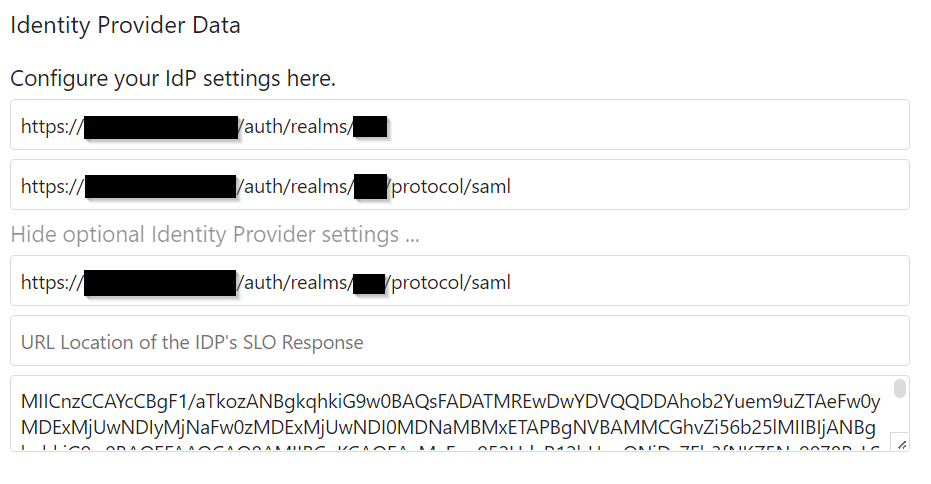
In the Identity Provider section enter in your Keycloak settings. The format is
https://<your domain name here>/auth/realms/<your realm name here>
The last text entry is the RSA public key from your Keycloak server. This is found in the Master realm --> Realm Settings --> Keys https://
Attribute mapping
I did not do any special Attribute mapping.
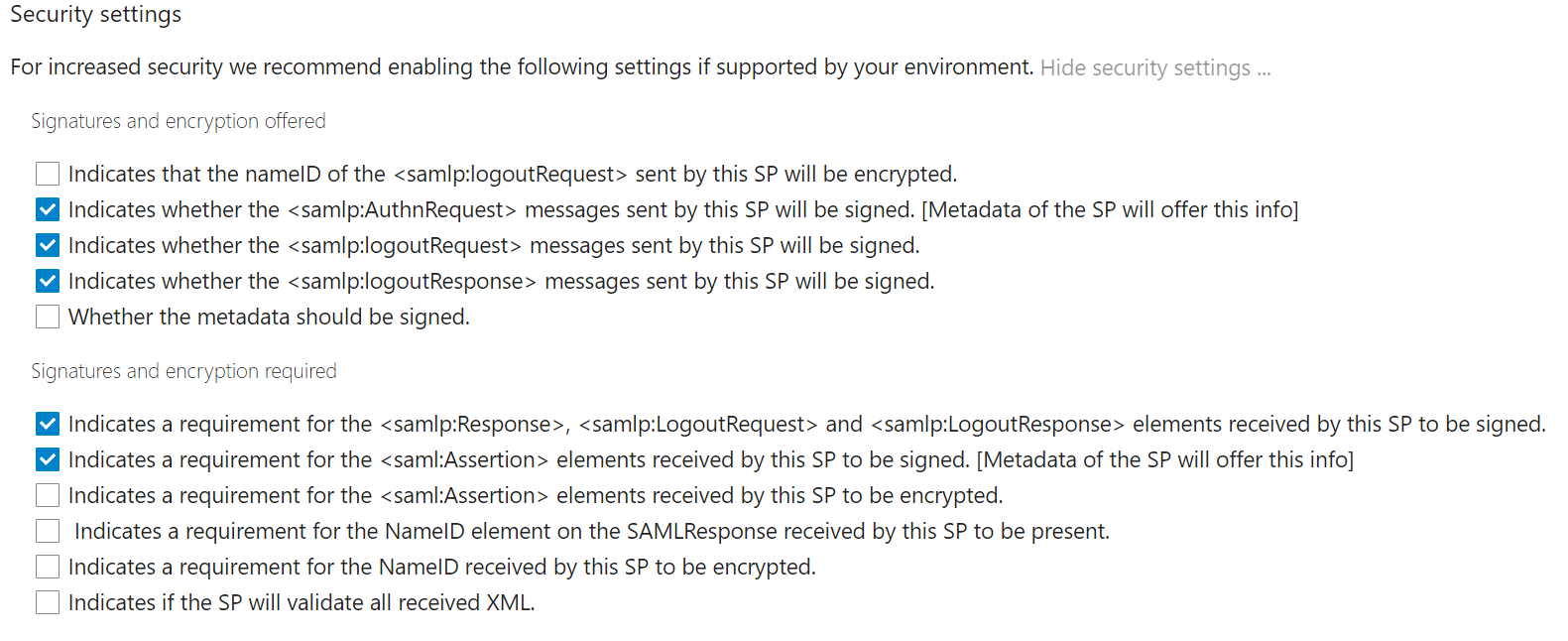
Security settings
Check the boxes to make it look like this:
Export XML
With the Nextcloud configuration complete you should have a gray indication "Metadata valid" next to the "Download metadata XML" button. Download the XML file so that you can import it into Keycloak.
Keycloak configuration
In Keycloak create a new client and choose to import a file. Upload the previously downloaded medata.xml and click ok.
Then go to the Mappers tab. If you do not need the role mapping, just delete it. I don't use it yet but I might look at this again in the future.
Then create a new Mappers:
Username
name: username
mapper type: user property
property: username
SAML attribute name: username
SAML attribute NameFormat: basic
Email
name: email
mapper type: user property
property: email
SAML attribute name: email
SAML attribute NameFormat: basic
Roles
name: Roles
mapper type: Role List
Role attribute name: Roles
Friendly name: roles
SAML Attribute NameFormat: Basic
Single Role Attribute: On
After the mappers are created and the client is saved, all Keycloak configuration is done. Open a new browser/Private Window and try to login to your Nextcloud account. If it doesn't work, check out the Nextcloud log file and the Keycloak log to determine where the breakdown is happening.